
Cómo Se Produce Un Ataque De Phishing Infografia Infographic Tics Y Vrogue
Check the Links: URL phishing attacks are designed to trick recipients into clicking on a malicious link. Hover over the links within an email and see if they actually go where they claim. Enter suspicious links into a phishing verification tool like phishtank.com, which will tell you if they are known phishing links.

What Should You Do If You Accidentally Click on a Phishing Link?
You can use EasyDMARC's phishing link checker by copying and pasting the URL into the search bar and clicking "Enter." You'll receive information about each link separately in a few seconds. You can also paste text containing links into the box. The tool checks for phishing URLs, simultaneously detecting and analyzing up to 20 links.
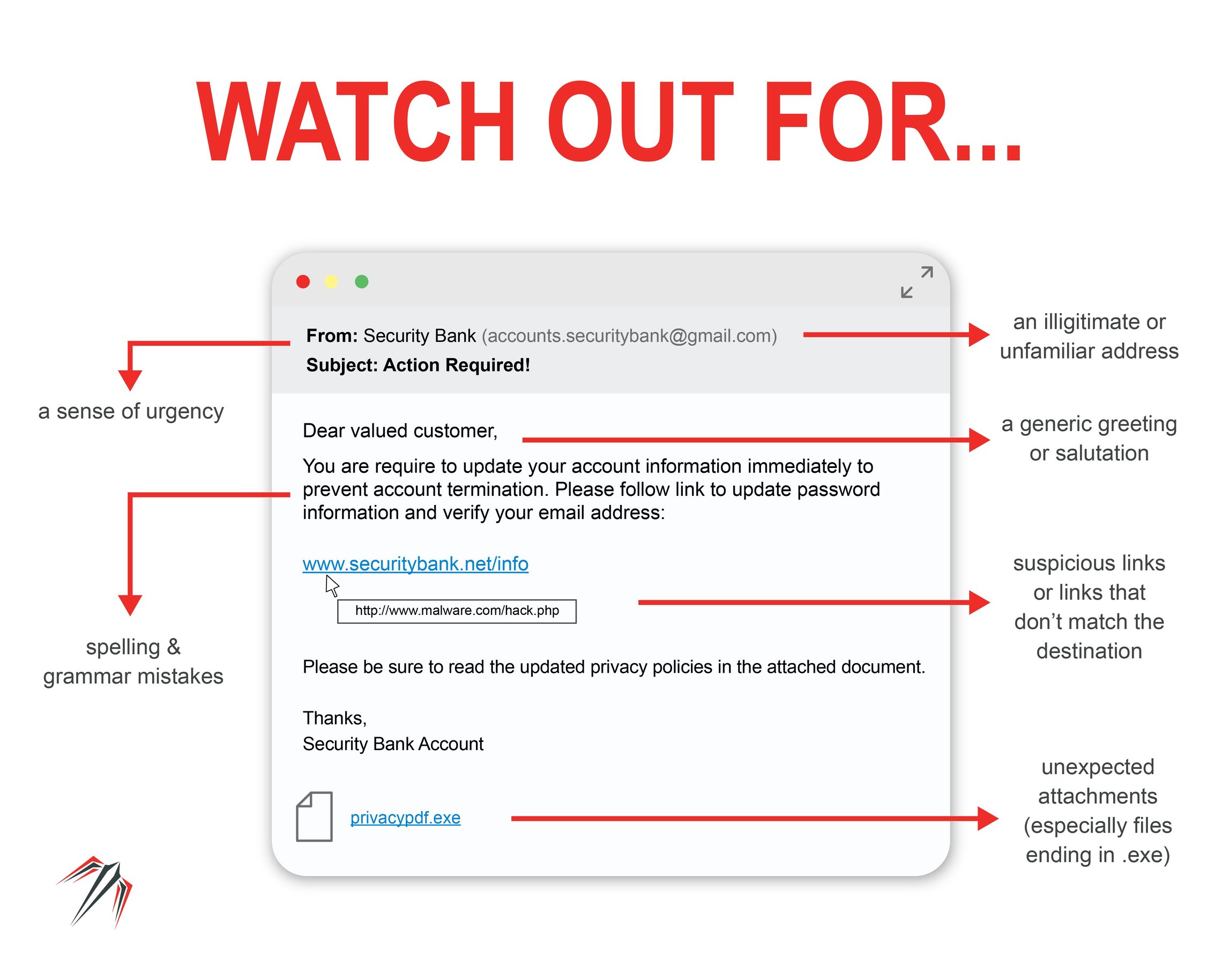
Don’t Get Hooked! 7 Signs of a Phishing Email
Whether you entered in any information or not, here's what you should do after clicking a phishing link, per cyber security company aNetworks: Disconnect your device from the internet to stop.
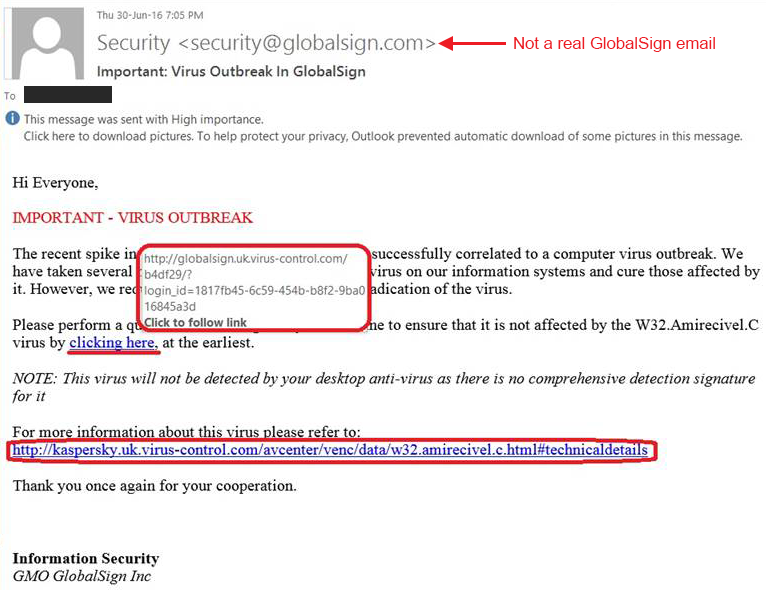
How to Spot a Phishing Website
URL phishing most often comes in the following forms: "Legit" links are phishing links that use legitimate websites, such as Google or Bing search engine results, to redirect the victim to websites they want, like this (this one is safe to check, but hover over the link to see where the URL leads first). Masked links are hyperlinks that are.

What Happens When You Open a Suspicious Link Phishing Emails and How Hackers Trick You
A click is just a click, usually. Most of the time, clicking a link just brings up a webpage. In the case of attempted phishing, the webpage may look like some other site you might recognize, but it won't be that site at all.Nine times out of ten, it'll be a sign-in page, and you'll be asked to sign in to the account the page is trying to look like.
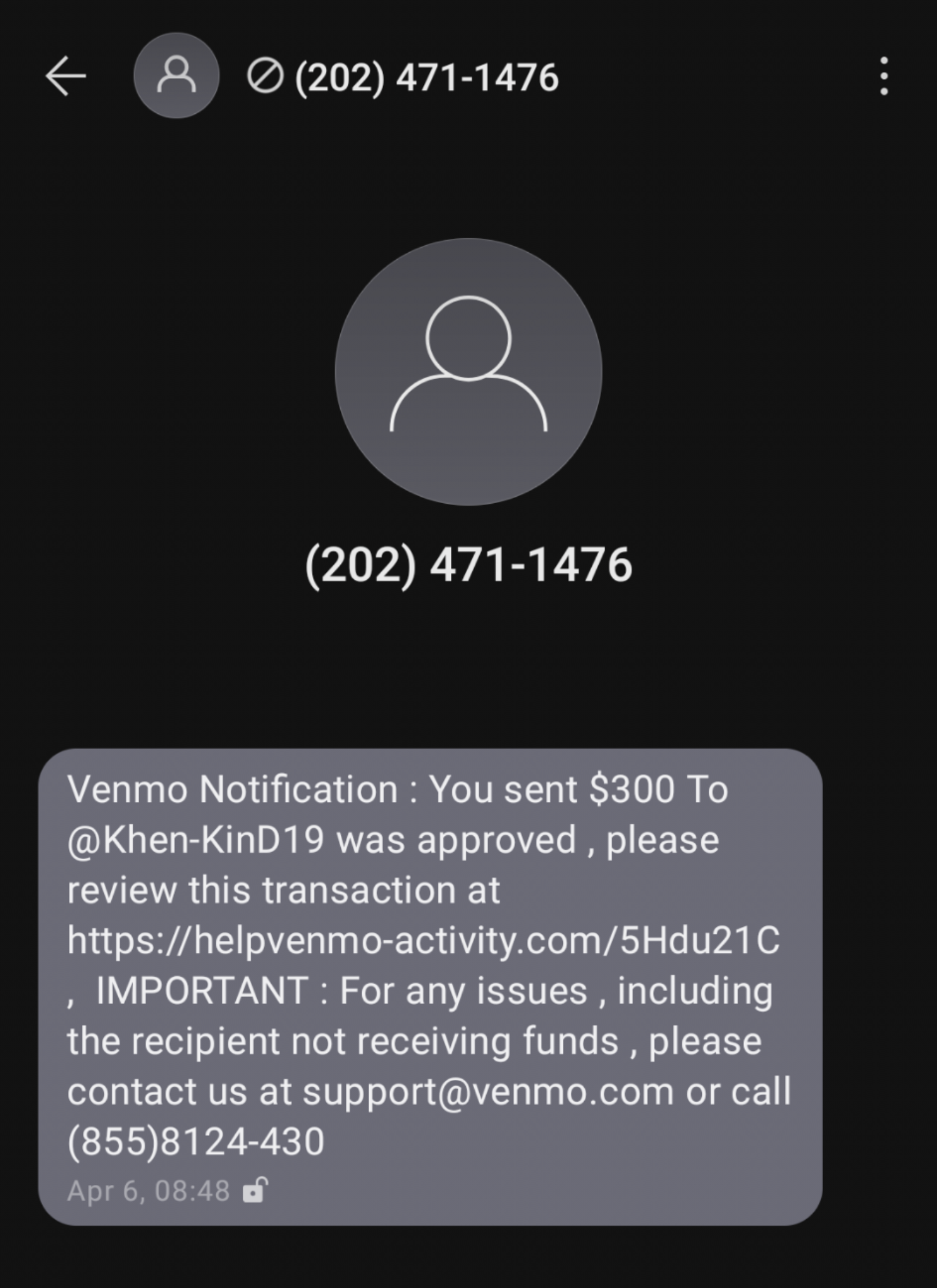
Clicked A Phishing Link? Here's What Happens & What To Do Now
To do this, hover over hyperlinked text and check the text that pops up at the bottom left of your browser. Hover over a link and check the hyperlink info in the bottom left bar. Remember, a fake link is trying its hardest to trick you into thinking it's real. So, a URL will try and imitate the real website as closely as possible.

Types of Phishing Attacks You Need to Know WebNIC
3. Delete any automatic downloads. If you see a download starting from your browser or on the right-hand side of your computer, you may assume that it's a system update. But you're probably the victim of a drive-by download attack [ * ]. In these attacks, scammers install malicious programs without your consent.
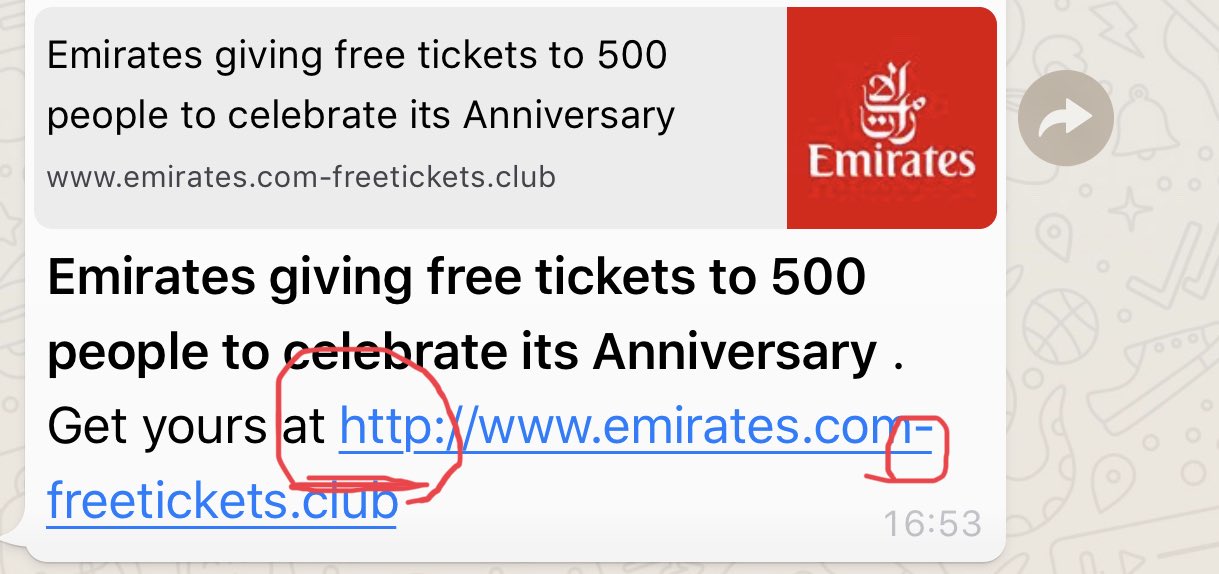
Crafting Phishing Links A Comprehensive Guide Computer Forensics World
Free URL check tool to detect phishing & fraudulent sites. Check. Scan URLs for Malware & Phishing Links

What To Do If You Click On A Phishing Link 2021 Guide
The process of creating a phishing link involves choosing a target, crafting a malicious URL, and designing a deceptive web page. These are the various phishing techniques and link spoofing methods that attackers use to make their links look legitimate: Using similar or misspelled domain names, such as paypa1.com instead of paypal.com.

How to Protect Your Business From a Phishing Attack
Overview. Phishing scams are almost always about links. While most people are generally aware that you shouldn't click on shady ones that come from strangers, there are a variety of clever ways in which web thieves try to cover their tracks. Here is a brief overview of some of the most common link manipulating tactics we've uncovered.

Phishing Attacks and How to Protect Against Them Office of the Victorian Information Commissioner
There are two parts to a link: The words describing the link (the part you see) and the URL. If you're on a computer, hover over the link and find out its real destination. If it doesn't match the link displayed, assume it's unsafe and don't click it. This is an easy, effective way of spotting phishing threats.
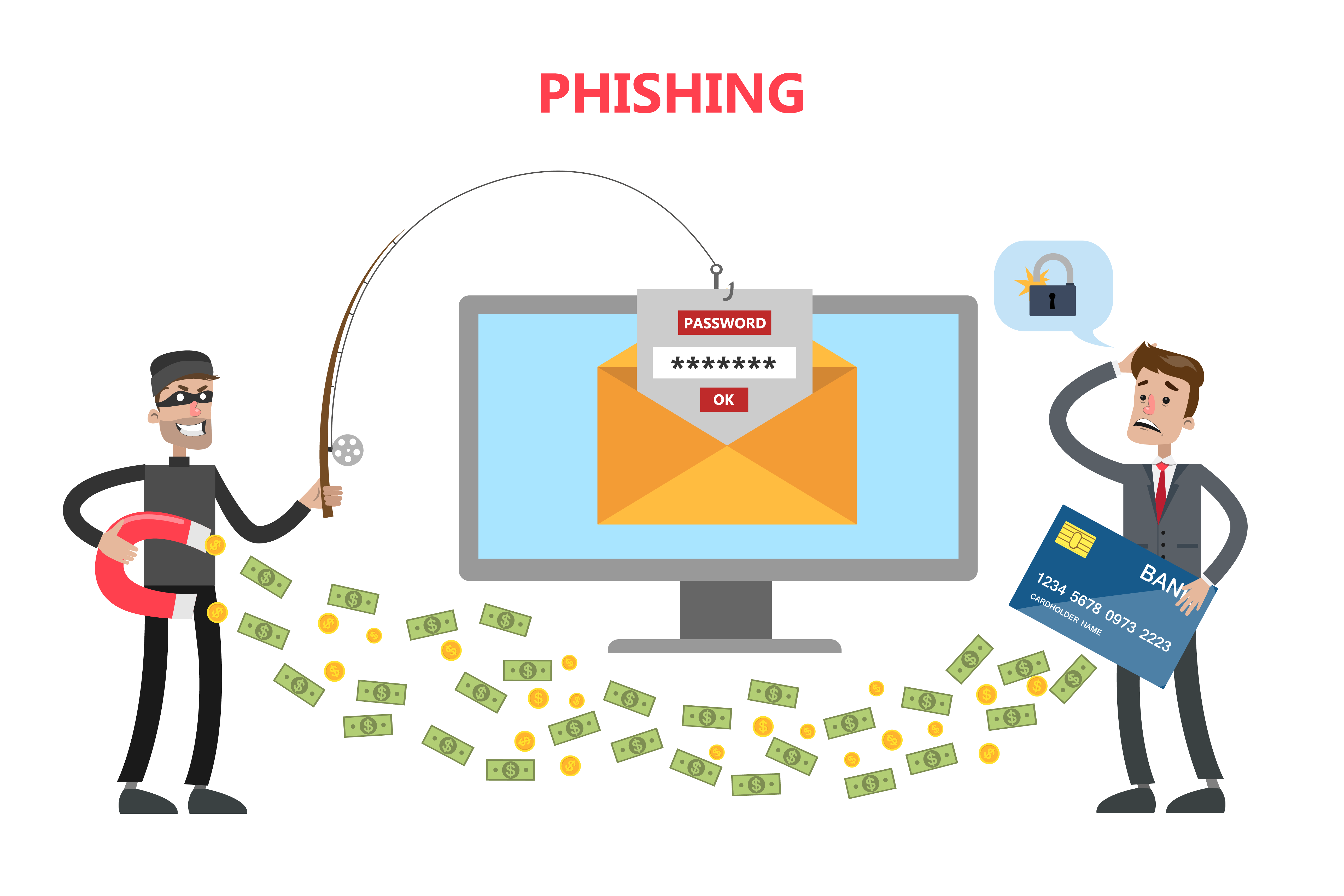
Things to know about Phishing attacks DEV Community
Phishing is a cyberthreat in which scammers try to lure sensitive information or data from you by disguising themselves as a trustworthy source. They do this using a variety of communication methods, including email, Google Chat, text messages, phone calls, and more. No matter which method scammers use, they want your personal information so.

Top 5 Most Common Phishing Attacks » The Merkle News
What happens if I click a phishing link? Phishing is the most prominent form of cyber-attack, regularly prompting email recipients into disclosing their personal information, credentials, downloading malware, or paying fraudulent invoices. Phishing can result in cybercriminals gaining unauthorized access to organizations' data, network.
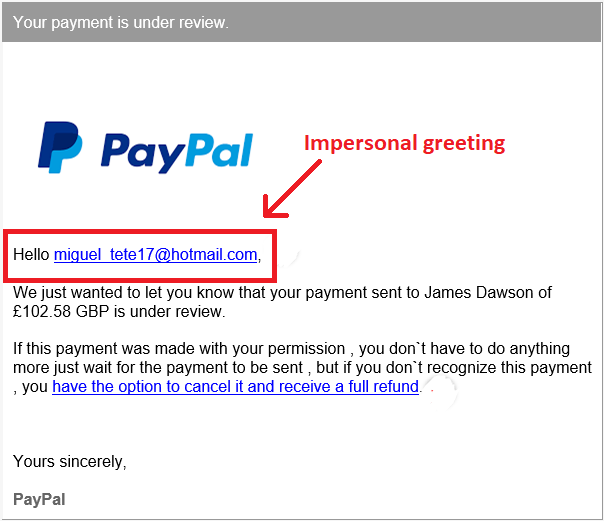
What to Do If You Click on a Phishing Link 4 Steps to Minimize Impact
Meet the Author Emily Jones, PMP, CMMC-RP. Emily Jones serves as the Principal Practice Leader for Warren Averett Technology Group. She has more than 30 years of experience, including a 12-year career at NCR Corporation, a world leader in transaction technologies, and 20 years with Jackson Thornton Accounting and Consulting in their technology group where she was a founding member.

How to Purify Your Device After Clicking a Phishing Link
3. The Google Docs worm (reloaded) In May 2017, a phishing attack called "the Google Docs worm" took the internet by storm, masquerading as Google Docs to gain deep access to users' emails and contact lists, recalled Wired's Lily Hay Newman. "The scam was so effective because the requests appeared to come from people the target knew.

How to Check a Link for Phishing EasyDMARC
EasyDMARC's phishing link checker is a great tool to detect phishing or malicious websites. It's easy to use—simply copy and paste the link into the search bar and click the "Enter" or the "Check URL" button. Our tool can check for phishing URLs, detecting and analyzing up to 20 links at once. It displays the link's URL status.