
Blueborne, un nuevo malware para Android En Clave Geek noticias de
Armis discovered BlueBorne, a new attack vector, endangering major mobile, desktop, and IoT operating systems, including Android, iOS, Windows, and Linux, and the devices using them. It includes 8 zero-day vulnerabilities, 4 of them critical. With BlueBorne, a hacker can take over your device or set up a man-in-the-middle attack.

BlueBorne Vulnerability Scanner for Android gHacks Tech News
BlueBorne is an attack vector by which hackers can leverage Bluetooth connections to penetrate and take complete control over targeted devices. It affects: - Mobile phones - Computers - IoT Devices Download BlueBorne Learn more about it through live demonstration of the attack here.

BlueBorne Exploit Malware Via Bluetooth 5.3Billion Devices Affected
The folks over at Armis Labs has just revealed a new attack vector that targets unpatched Android, iOS, Windows, and Linux devices with Bluetooth enabled. The exploit has been named BlueBorne.

Blueborne Android Take Over Demo YouTube
BlueBorne download the one of the most powerful bluetooth hacking tool for smartphones. Blueborne is a very powerful bluetooth hacking tool for the security researcher and penetration testers to penetrate into various bluetooth powered devices to gain full control over them. It can attack on a wide range of bluetooth powered equipment like.

[Download] Use the official BlueBorne Vulnerability Scanner app to
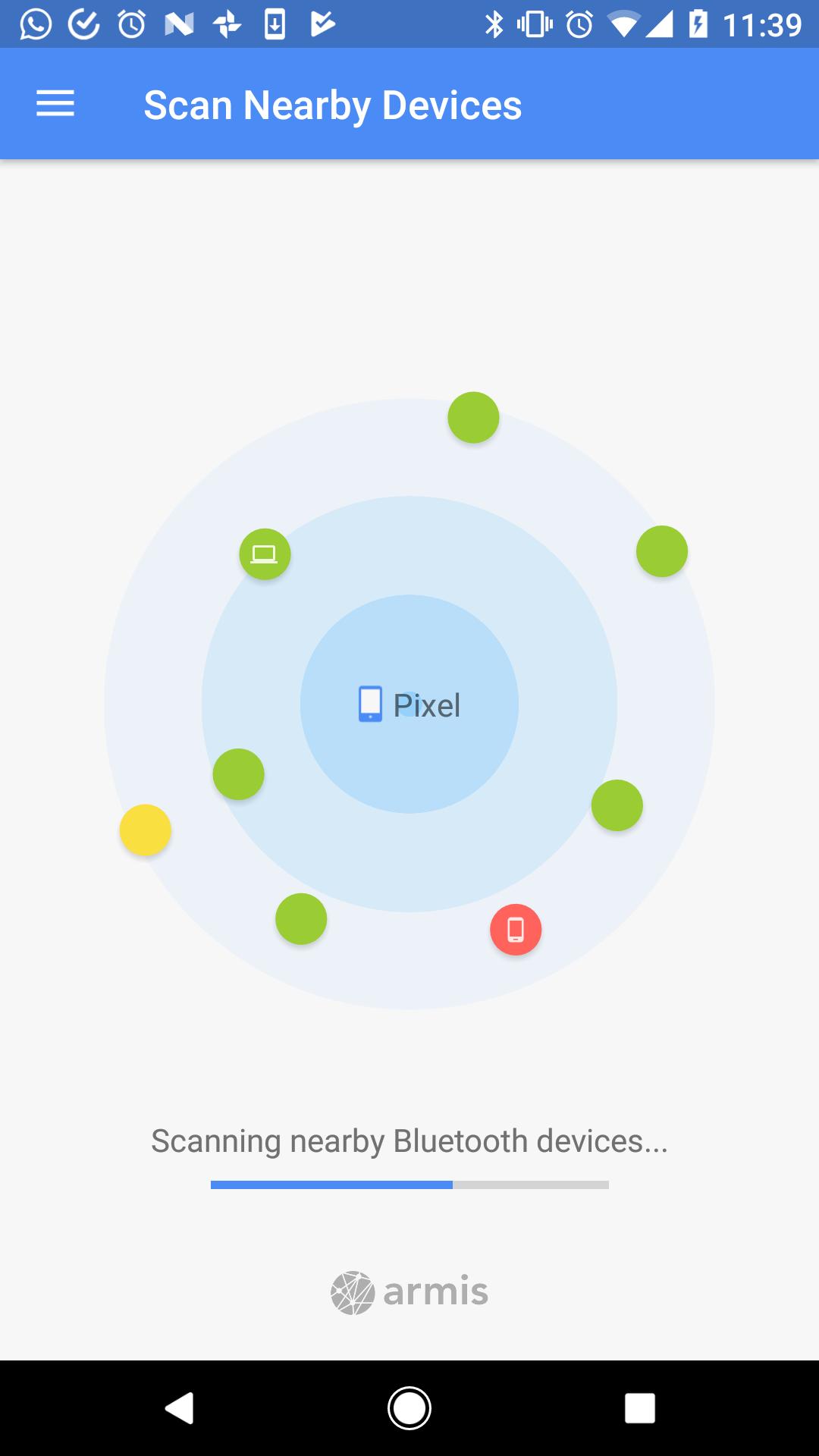
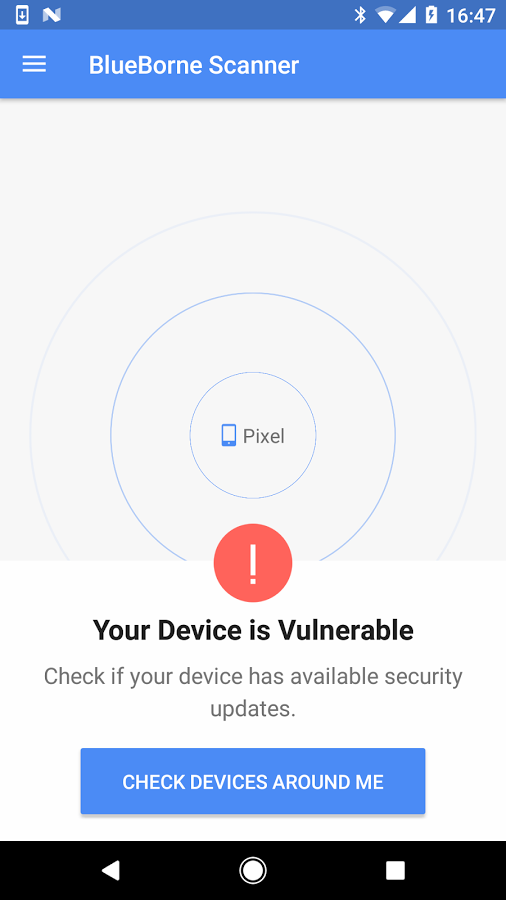
BlueBorne Vulnerability Scanner by Armis..Note: As I'm Using Virtual Android Emulator..Check to see if your device - or those around you - is vulnerable.

BlueBorne killchain on Dockerized Android SecSI
BlueBorne concerns us because of the medium by which it operates. Unlike the majority of attacks today, which rely on the internet, a BlueBorne attack spreads through the air. This works similarly to the two less extensive vulnerabilities discovered recently in a Broadcom Wi-Fi chip by Project Zero and Exodus. The vulnerabilities found in Wi-Fi.
blueborne apk Download APK files free online downloader
Armis discovered BlueBorne, a new attack vector, endangering major mobile, desktop, and IoT operating systems, including Android, iOS, Windows, and Linux, and the devices using them. It includes 8 zero-day vulnerabilities, 4 of them critical. With BlueBorne, a hacker can take over your device or set up a man-in-the-middle attack.

Descarga de APK de BlueBorne Security Scan & check for patches para
Add this topic to your repo. To associate your repository with the blueborne topic, visit your repo's landing page and select "manage topics." GitHub is where people build software. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects.
BlueBorne Attack SureLock To The Rescue
Get BlueBorne old version APK for Android. Download. About BlueBorne. English.. BlueBorne is a series of simple attacks on various parts of the Bluetooth stack running on almost every smart device in the world including 2 billion Android phones. Stay safe and be secure! Turn off the blueooth to secure yourself against BlueBorne!

Eerskraft Mod Apk Downlaod for Android
BlueBorne is a type of security vulnerability with Bluetooth implementations in Android, iOS, Linux and Windows. It affects many electronic devices such as laptops, smart cars, smartphones and wearable gadgets. One example is CVE-2017-14315. The vulnerabilities were first reported by Armis, the asset intelligence cybersecurity company, on 12.

BlueBorne Vulnerability Scanner Detector Guide APK for Android Download
This is what BlueBorne can do. Naturally, cyber criminals can deploy any type of malicious software they want, from banking Trojans to ransomware and info-stealers. Even the list of most common cyber attacks is quite long. By using BlueBorne, attackers can: Infect devices and ask for ransom; Steal your sensitive data; Spy on your browsing habits

Kwikset Security The BlueBorne Threat Kwikset Locks Smart Security
In this demo, Armis Labs will demonstrate BlueBorne, and how a hacker can take over an android device only via bluetooth. What is BlueBorne?It endangers maj.

BlueBorne Bluetooth Attack Android, Linux, Window YouTube
We got to see something cool and terrible (yes, it's possible to be both at the same time) earlier this week when Armis Security published the details of a new Bluetooth exploit.Called "Blueborne.
Скачать BlueBorne Scanner 1.07 для Android
Bluetooth is the leading and most widespread protocol for short-range communications. According to estimates , more than 8.2 billion Bluetooth devices are currently in use, and the number grows by the day.

BlueBorne Vulnerability Scanner Checks if Your Device is Vulnerable
The BlueBorne attack vector can be used to conduct a large range of offenses, including remote code execution as well as Man-in-The-Middle attacks. "BlueBorne affects pretty much every device we.
GitHub Kogl1n/Blueborne Blueborne Android Bluetooth vulnerability
To test this, the BlueBorne Vulnerability Scanner was downloaded from Google Play Store and installed on a device emulator. Reverse engineering this app shows the local device risk check simply compares the device security patch date to a hardcoded date around the time of disclosure, and the remote (nearby) devices risk check and rating is a.