
Network Security Risk Assessment Template SampleTemplatess SampleTemplatess
1. Identify company assets and infrastructure. Categorize the assets based on their importance and risk level. Conduct internal and external vulnerability scans. Document the vulnerabilities found. Approval: Documented Vulnerabilities. Perform a threat analysis. Review the threats and their potential impact. Approval: Potential Threats Impact.
Security Risk Assessment Checklist Template
Application security risk assessment checklists can help organizations determine which areas of their application environment need additional protection or attention to ensure that their systems remain secure from malicious actors. Every application is unique and carries threat factors.

Free Security Assessment Template and Examples
This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A-130, Appendix IV: Analysis of Key Sections.

Explore Our Sample of Security Risk Assessment Checklist Template for Free Assessment
What are the Steps of a Cyber Risk Assessment? STEP ONE: Identify and Document Network Asset Vulnerabilities4 Characterizing or inventorying network components and infrastructure, including hardware, software, interfaces, and vendor access and services will help determine possible threats.

FREE 10+ Sample Risk Assessment Checklist Templates in Google Docs Word Pages PDF in 2023
A security risk assessment should be performed annually, if not quarterly. Consider using a checklist — such as the xlsx file from TechRepublic Premium — to not only coordinate security.
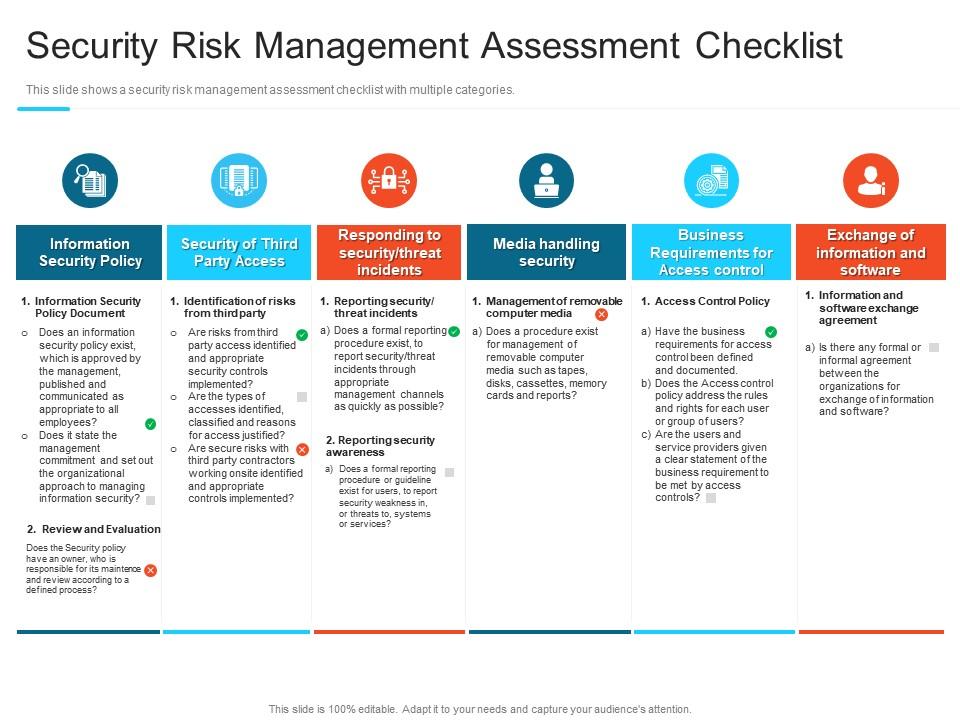
Security Risk Management Assessment Checklist Steps Set Up Advanced Security Management Plan
The Security Risk Assessment Checklist is a tool used to assess the security risks of an IT system. It consists of a set of questions and check boxes that help identify potential risks and vulnerabilities. It looks at areas such as system architecture, authentication, encryption, network security, user access, and system logging.

Business Risk assessment Template New 10 Sample Security Risk assessment Templates Pdf Word
Now that you know what you should gain, let's go over the eight steps involved with our cyber security risk assessment checklist: 1. Identify the high-value assets across your organization that could be impacted by threats. Common examples include servers, domains, trade secrets, customer credit card data, and other sensitive client information.

Physical Security Risk Assessment Template merrychristmaswishes.info
Security assessments have specific objectives, acceptable levels of risk, and available resources. Because no individual technique provides a comprehensive picture of an organization's security when executed alone, organizations should use a combination of techniques.

physical security risk assessment software smilymezquita99
This information security risk assessment template includes a column for ISO 27001, so you can apply any of the International Organization for Standardization's (ISO's) 14 information security standards steps to each of your cybersecurity risks.. Use this cybersecurity risk assessment checklist template to meet your cybersecurity goals.

Data Security Risk Assessment Checklist
Step 3: Analyze risks and determine potential impact. Now it is time to determine the likelihood of the risk scenarios documented in Step 2 actually occurring, and the impact on the organization if it did happen. In a cybersecurity risk assessment, risk likelihood -- the probability that a given threat is capable of exploiting a given.
FREE 6+ Security Assessment Templates in PDF MS Word
Drive Efficiency With Centralized IT Assets, Automated Risk Scoring, & Project Management. Built by ITRC Experts to Meet Your Exact Needs. Enable Org-Wide Collaboration & Adoption

Security Assessment Template 18+ (Word, Excel & PDF Format)
A security risk assessment is a process that helps organizations identify, analyze, and implement security controls in the workplace. It prevents vulnerabilities and threats from infiltrating the organization and protects physical and informational assets from unauthorized users. Requirements
35+ Free Risk Assessment Forms Smartsheet
What is Security Risk Assessment? Security risk assessment is performed to allow organizations identify and assess security posture. The assessment's primary purpose is to inform decision-makers about the security risks that might surface in the organization and ease risk handling.

Browse Our Example of Security Risk Assessment Checklist Template Assessment checklist
A facility security assessment checklist helps a facility security officer (FSO) carry out an extensive internal scan of a facility's current infrastructure and its vulnerabilities and potential threats. It helps define the necessary solutions to achieve their desired future state of security through a Facility Security Plan (FSP). In this article
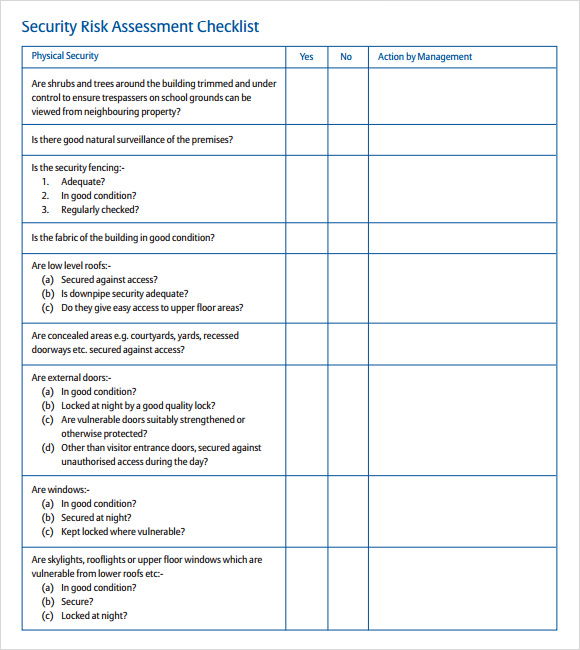
FREE 12+ Sample Security Risk Assessment Templates in PDF MS Word Excel
Using a cyber security risk assessment checklist can help you understand your risks and strategically enhance your procedures, processes and technologies to reduce the chances of financial loss. This document explains the key elements of an effective checklist. Checklist: Essential Elements of a Security Risk Assessment

Building Security Risk assessment Template Elegant Home Building Checklist Template Security
The NIST Risk Management Framework (RMF) provides a comprehensive, flexible, repeatable, and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems and links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal Information Security.